AWS Cloud watch Auto scaling alarm [PROJECT - 4]
This project implements an automated scaling solution using AWS CloudWatch Alarms to dynamically adjust EC2 instances based on real-time metrics (e.g., CPU utilization, memory, or network traffic). By setting up threshold-triggered alarms, the system scales resources up/down via Auto Scaling Groups (ASG), ensuring cost-efficiency and high availability. The solution enhances performance during demand spikes while reducing costs during low-traffic periods.
3/26/20253 min read


Project Title: AWS Auto Scaling with CloudWatch Alarms, VPC, ALB, and Secure Subnet Architecture
Project Overview
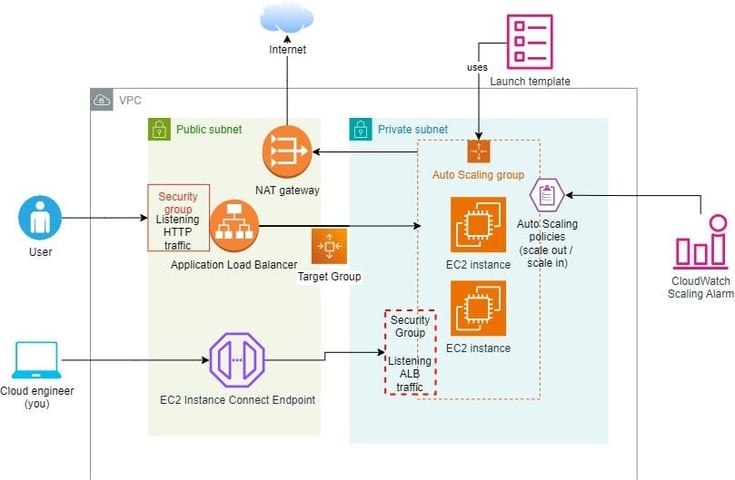
Designed and deployed a highly available, auto-scaling AWS infrastructure leveraging CloudWatch Alarms, Application Load Balancer (ALB), and a secure VPC architecture with public and private subnets. The system dynamically scales EC2 instances based on real-time performance metrics (CPU, memory, network) while maintaining security best practices by isolating backend instances in private subnets.
Key Components & Implementation
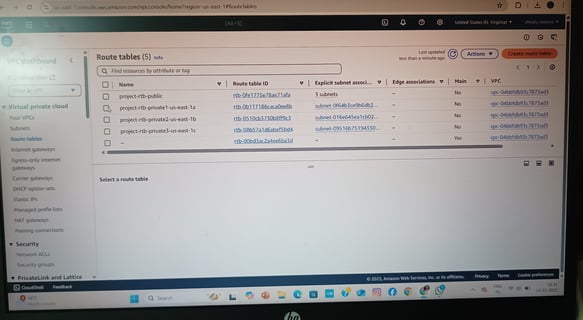
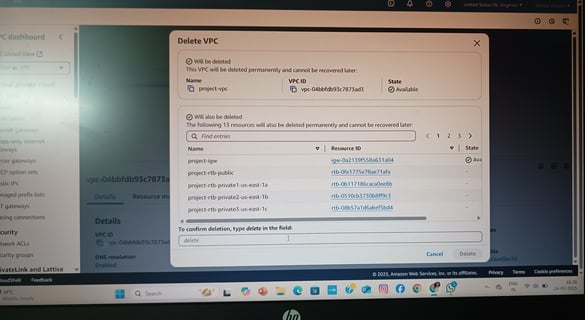
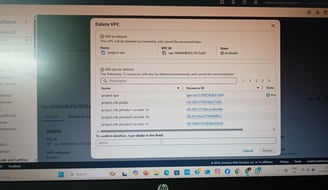
VPC & Network Architecture
Created a custom VPC with public and private subnets across multiple Availability Zones (AZs) for fault tolerance.
Public Subnets: Hosted Internet-facing resources (ALB, NAT Gateway).
Private Subnets: Secured backend EC2 instances (no direct internet access).
Configured Route Tables, Internet Gateway (IGW), and NAT Gateway for controlled traffic flow.
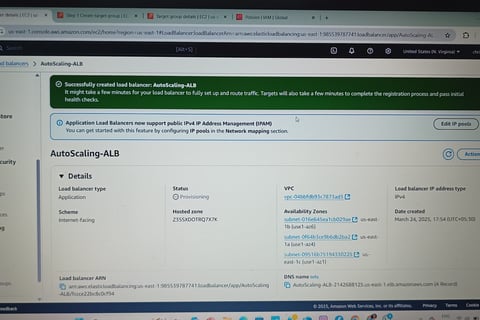
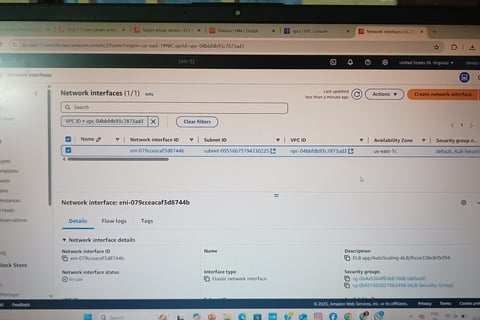
Application Load Balancer (ALB) in Public Subnet
Deployed an ALB in public subnets to distribute traffic across auto-scaled EC2 instances.
Configured Target Groups for health checks and routing.
Enabled HTTPS (SSL/TLS) for secure communication (optional).
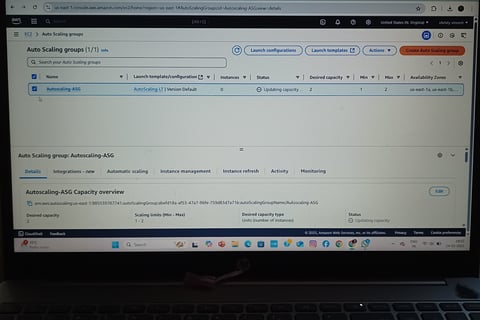
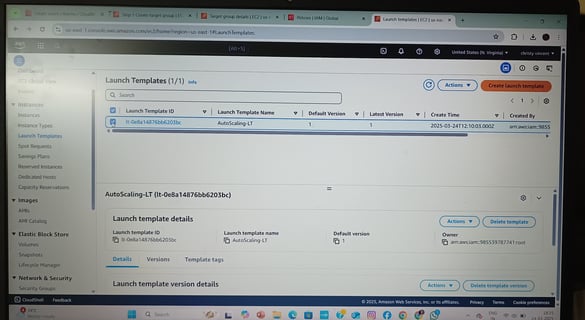
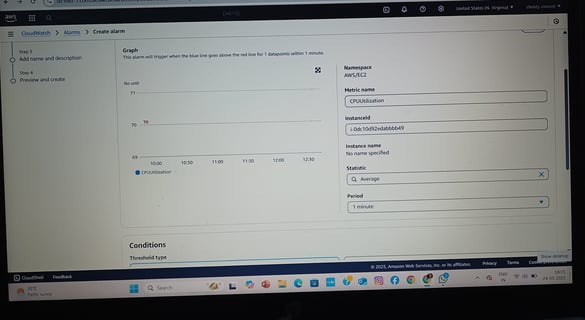
Auto Scaling Group (ASG) with CloudWatch Alarms
Set up Launch Templates to define EC2 configurations (AMI, instance type, user data).
Created Auto Scaling Policies for:
Scale-Out: Triggered when CPU > 70% (add instances).
Scale-In: Triggered when CPU < 30% (remove instances).
Integrated CloudWatch Alarms to monitor metrics and trigger scaling events.
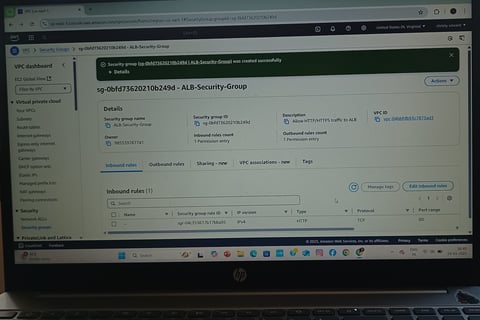
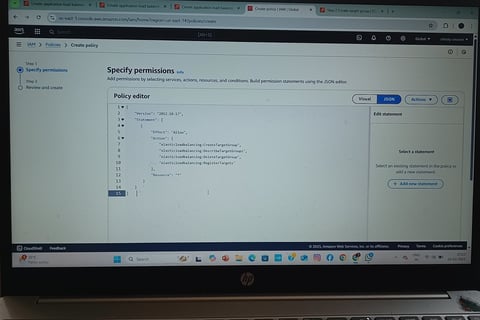
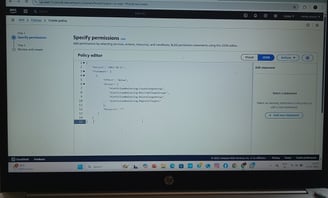
Security & IAM Policies
Applied IAM Roles & Policies to grant least-privilege permissions to EC2 instances (e.g., CloudWatch access).
Used Security Groups to restrict traffic:
ALB (HTTP/HTTPS from the internet).
EC2 Instances (only allow traffic from ALB).
High Availability & Fault Tolerance
Distributed instances across multiple AZs for resilience.
Ensured self-healing—failed instances are automatically replaced.
Why This Project?
Optimized Cost & Performance: Auto-scaling reduces costs during low traffic while handling spikes efficiently.
Secure Architecture: Backend instances in private subnets are protected from direct exposure.
Real-World Applicability: Mimics production-grade AWS setups used in scalable web apps.
Technologies Used
AWS Services: EC2, VPC, ALB, CloudWatch, Auto Scaling, IAM, NAT Gateway, Route 53.
Concepts: High Availability, Fault Tolerance, Horizontal Scaling, Infrastructure as Code.
AWS PROJECT IMAGES
### GitHub Project Summary: AWS Auto Scaling with CloudWatch, VPC & ALB
Project Name: `aws-cloudwatch-autoscaling-alb-vpc`
Description:
A scalable AWS infrastructure using CloudWatch Alarms, Auto Scaling Groups (ASG), and an Application Load Balancer (ALB). Features:
- Secure VPC with public/private subnets (NAT Gateway, IGW).
- ALB in public subnet routing traffic to private EC2 instances.
- Auto Scaling triggered by CloudWatch (CPU/memory metrics).
- IAM policies & Security Groups for least-privilege access.
Tech Stack: AWS (EC2, VPC, ALB, CloudWatch, IAM), Terraform (optional).
Key Files/Directories:
- `terraform/` (IaC) or `aws-cli-commands.md` (manual setup).
- `architecture-diagram.png` (VPC + ALB flow).
- `README.md` (deployment steps, thresholds).
Why It’s Useful: Demonstrates cost-optimized, production-ready AWS scaling with security best practices.
--- 🚀
LINK -


